Some time ago far from here and close to there, one of the first container that has been implemented in my docker environment was PiHole to filter traffic, get rid of ads and improve quality of internet life for me and family.
Read more: Pi in the holeLater, usage of this product was suspended due number of some restrictions and first of them was, eventually, networking. At the last place I got unmanageable router from provider with centrally-managed DNS servers, that makes usage almost impossible. Second challenge was related with usage of 2 routers simultaneously – one (old Zyxel Keenetic Giga 3) was responsible for infrastructure part and workplace, and another one (provider’s) keep home clients connection.
This setup was acceptable, except part, that infra router has been a part of NAT of provider’s one. On one hand – it works and VPN on infra router was able to work, on other hand provider’s router clients wasn’t able to consume infra services at scale, that adds some complexity for management.
With new ISP, new router I got a great opportunity to merge these two networks and improve it in general.
Let me give a basic network example of initial setup.
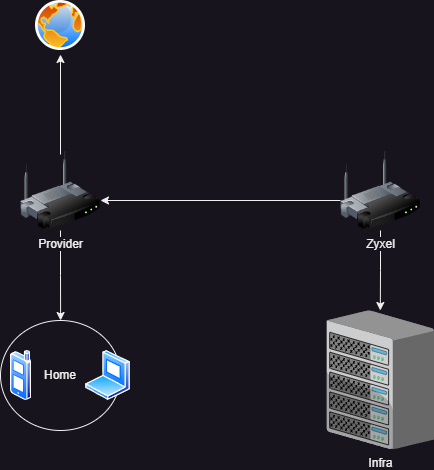
And logical setup
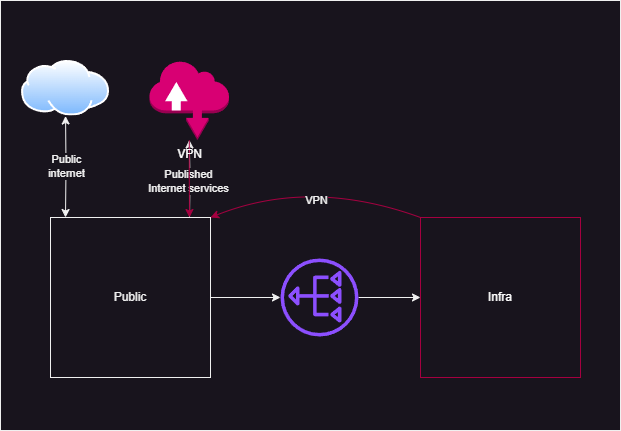
As you can see, Infra network was able to interact and communicate with Public network, but not vice-versa. And here we come to the first problem, that we need to solve – create a route back to infra router to connect these two networks. This challenge needs admin access to the provider router, that, by some reasons, persist only partially, and route persist in some unavailable parts. Luckily, someone in internet was able to solve this puzzle with quite interesting hack. Long story short:
- Preparing USB with script
- Inserting it in providers router
- Adjusting DynDNS with custom script pointing to our script and setting timezone as close to midnight as we can
- Picking up passwords at 1 minute after midnight.
So, with this elegant solution we solve first part of our puzzle and ready to go ahead. With admin access we are able to create a route back to our infra router and get and access from Public network to Infra network.
Looks like this is the end of story, but, it’s just a first part of it.
To finish with the network part I have to ensure, that all the clients are able to pick up DNS, AD services and so on, and here I got a nice surprise – after some time, DNS stopped responding in public network. Seems quite strange, but….
Trying to get down to the problem, I even have to check traffic on DC to ensure, that the problem not related with some DC self-defense of DNS itself. At the end of this journey faulty element was found – it was Infra router DNS rebind-protect that just block traffic to the internal DNS assuming, that this is DNS-rebind attack. So, obviously, everything, that was coming from public network got blocked.
In the morning problem appears again, and this time it was related with faulty route to the routing table, that looks like this – 192.168.1.1/32. Here the problem were hiding in DHCP settings of the infra router client that replaced DNS servers with public ones. Once DNS configuration for this client were disabled, it started working properly.
So, completion of the network part move us to pihole, finally.
Idea is to setup it after DC to keep all of the request as much inside as it possible, so, preciseness of client have been sacrificed in the name of “privacy”.
Deployment itself, comparing with other mess looks like more predictable and straightforward – I used homebrew helm chart with Load balancer.
That’s almost it. Rest of the configuration – it’s just a pointing for new DNS and testing.
But the main intention of this article is to share totally different experience about well-known service. It could be deployed and done in many different ways with thousands of different problems, that keeps you up-to-date(?).
In reality, this is the continuation of small series here, that was written in Russian some time ago, and require some refactoring for future.
Feel free to share ideas and point out issues in this setup, I would be appreciate any advises.
Thanks for reading.

One reply on “Pi in the hole”
[…] everyone ignore bright idea of putting PiHole in k8s let´s talk about other Pi and another Hole. As every “bright” idea is coming from […]