I’m looking through a hole in the sky
Black Sabbath – Hole in the sky
I’m seeing nowhere through the eyes of a lie
I’m getting closer to the end of the line
I’m living easy where the sun doesn’t shine
As everyone ignored bright idea of putting PiHole in k8s let´s talk about other Pi and another Hole.
As every “bright” idea is coming from need, this one is a good example. In previous opus was performed an attempt to explain how to create network issues without need with PiHole on top, but now it was a different kind of need – I have to control my overgrown homelab without affect on all service consumers.
So, at the very last moment before the business trip in my memory float obvious problem – I cannot connect from outside.
I understand, that normal modern guys are already in the skies and don’t worry about this problem, but here, at the land of on-premises solutions, we have to reinvent bicycles again and again.
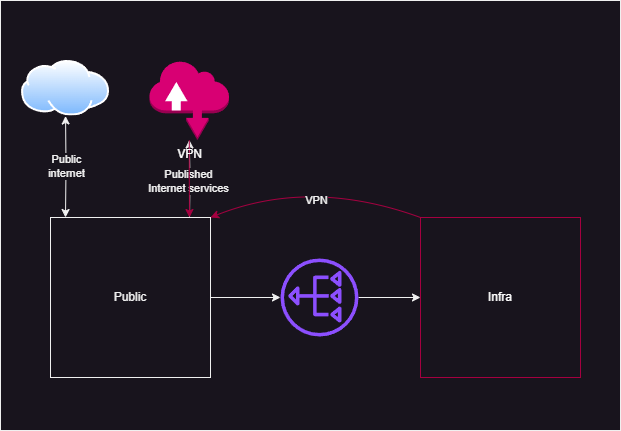
I mean, sure I can, but connection to the public VPN address is possible, but further management not challenging but insecure, because will require additional holes in firewall, that not looks good.
Another option was installation of VPN server inside the server, that sounds promising, but in case of something, this will be single point of failure, as exactly this server needs to be fixed.
So, front door in vulnerable and should be avoided for management, usage of infranet is discussible and won’t give any redundancy. Implementation of router-based VPN server doesn’t looks good, as old home router not powerful enough to keep several different VPN sessions. Let’s go some kind of other options.
And, here we go – PiVPN, installed on dusty and almost forgotten RasberryPi 3B. Some leftovers after StupidHome never-ending story. Benefits are obvious – separate device, that even can run on powerbank, wifi interface that can giving sufficient flexibility in placement of your secret door and, because it can connect to any 2.4 GHz routers, it could be used on provider router. Required preparation – white IP, in my case, something managed by semi-DynDNS with godaddy API.
Step-by-step plan.
- Acquire “white IP” from your provider
- Validate bash script, like this for godaddy, as example. Obviously, any other DynDNS solution with require some other options. Pay attention to the environment, as in prod and dev it will be different URL’s for different scenarios.
- Prepare port forwarding on router and install PiVPN. Great thing about this particular package is not only about simplicity, but also 2 options – Wireguard and OpenVPN, that can be useful in different cases. I don’t think that anyone need my comments about installation process, as it as straightforward as possible. Most of the issues here might be related with networking and DNS setup. DNS part might be skipped, is you don’t need to connect over fancy name.
- Actually, that’s it. If you’ve been careful enough you have at this moment of time running tiny VPN, that could be hidden anywhere.
2 weeks testing with remote access through this configuration demonstrated outstanding performance even on 3b with Wireguard onboard.
Intention of this article is not about to demonstrate bright idea, but mostly about great opportunities of small solutions and availability of quite robust open-source solutions, that finally become semi-user-friendly.
